SalamiAttack
All Star
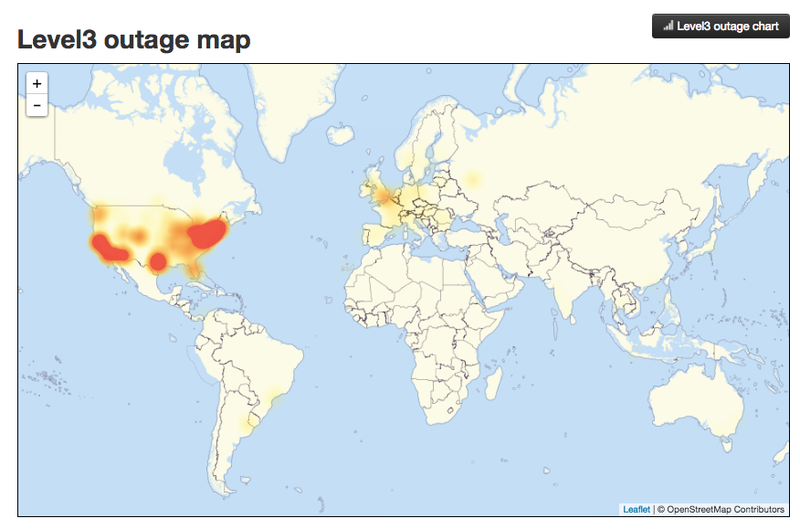
Government probes major cyberattack causing internet outages
Digital assailants affiliated with the hacking collective Anonymous appeared to take credit for at least a portion of the ongoing siege, indicating that it was retaliation for the Ecuadorian government's decision to cut off internet access for WikiLeaks founder Julian Assange over his site's ongoing leaks of alleged internal documents from Hillary Clinton's presidential campaign.
The digital assault affected internet users along the East Coast, and caused hundreds of sites to be inaccessible both early in the morning, and then again around midday.











shyt HAS BEEN ALL DAY.
Status overview | Down Detector
List of sites that currently down:
Box.com
Twitter.com
Schoology and Apex
Npmjs.com (Node Package Manager (major javascript package manager)
Roblox.com
Github.com
Spotify.com
Shopify.com
Freshbooks.com
Netflix.com (slow loading time)
The Boston Globe
The New York Times
PayPal
Theverge.com
Pinterest.com
Constantcontact.com
Playstation Network (PSN)
Revcontent.com
Fox News
Elder Scrolls Online
Starbucks rewards/gift cards
Braintree
Zoho CRM
xbox.com
Indeed.com
ActBlue
Grubhub
Kayak
Basecamp
Yammer
Ancersty.com
Mashable
Intercom.com
Disqus
Eventbrite
Wufoo.com
Iheart.com (iHeartRadio)
Business Insider
Imgur
NHL.com
Cleveland.com
Credit Karma
Squarespace Customer Sites
Atom.io
Wikia
Weebly
nimbleschedule.com
Okta
Big cartel
Zendesk.com
Blue Host
dailynews.com
Twillo
Intercom
donorschoose.org
Eve Online
Weather.com
PagerDuty
Recode
Wix Customer Sites
Speed Test
Salsify.com
Yelp
People.com
Wired.com
Genonebiology.com
Guardian.co.uk
HBO Now
youneedabudget.com
time.com
Qualtrics
BBC
Etsy
CNN
Urbandictionary
SBNation
Zillow.com
WSJ.com
Bill.com
WhatsApp.com
Digital assailants affiliated with the hacking collective Anonymous appeared to take credit for at least a portion of the ongoing siege, indicating that it was retaliation for the Ecuadorian government's decision to cut off internet access for WikiLeaks founder Julian Assange over his site's ongoing leaks of alleged internal documents from Hillary Clinton's presidential campaign.
The digital assault affected internet users along the East Coast, and caused hundreds of sites to be inaccessible both early in the morning, and then again around midday.











shyt HAS BEEN ALL DAY.
Status overview | Down Detector
List of sites that currently down:
Box.com
Twitter.com
Schoology and Apex
Npmjs.com (Node Package Manager (major javascript package manager)
Roblox.com
Github.com
Spotify.com
Shopify.com
Freshbooks.com
Netflix.com (slow loading time)
The Boston Globe
The New York Times
PayPal
Theverge.com
Pinterest.com
Constantcontact.com
Playstation Network (PSN)
Revcontent.com
Fox News
Elder Scrolls Online
Starbucks rewards/gift cards
Braintree
Zoho CRM
xbox.com
Indeed.com
ActBlue
Grubhub
Kayak
Basecamp
Yammer
Ancersty.com
Mashable
Intercom.com
Disqus
Eventbrite
Wufoo.com
Iheart.com (iHeartRadio)
Business Insider
Imgur
NHL.com
Cleveland.com
Credit Karma
Squarespace Customer Sites
Atom.io
Wikia
Weebly
nimbleschedule.com
Okta
Big cartel
Zendesk.com
Blue Host
dailynews.com
Twillo
Intercom
donorschoose.org
Eve Online
Weather.com
PagerDuty
Recode
Wix Customer Sites
Speed Test
Salsify.com
Yelp
People.com
Wired.com
Genonebiology.com
Guardian.co.uk
HBO Now
youneedabudget.com
time.com
Qualtrics
BBC
Etsy
CNN
Urbandictionary
SBNation
Zillow.com
WSJ.com
Bill.com
WhatsApp.com
.jpg)