How to: Understand and Circumvent Network Censorship
This is an overview of network censorship, but it is not comprehensive. Governments, companies, schools, and internet providers sometimes use software to prevent their users from accessing certain websites and services that are otherwise available on the open web. This is called internet...
< TOOL GUIDES
How to: Understand and Circumvent Network Censorship
Last Reviewed: February 01, 2024This is an overview of network censorship, but it is not comprehensive.
Governments, companies, schools, and internet providers sometimes use software to prevent their users from accessing certain websites and services that are otherwise available on the open web. This is called internet filtering
 or blocking
or blocking , and it is a form of censorship. Filtering comes in different forms. Even with encryption
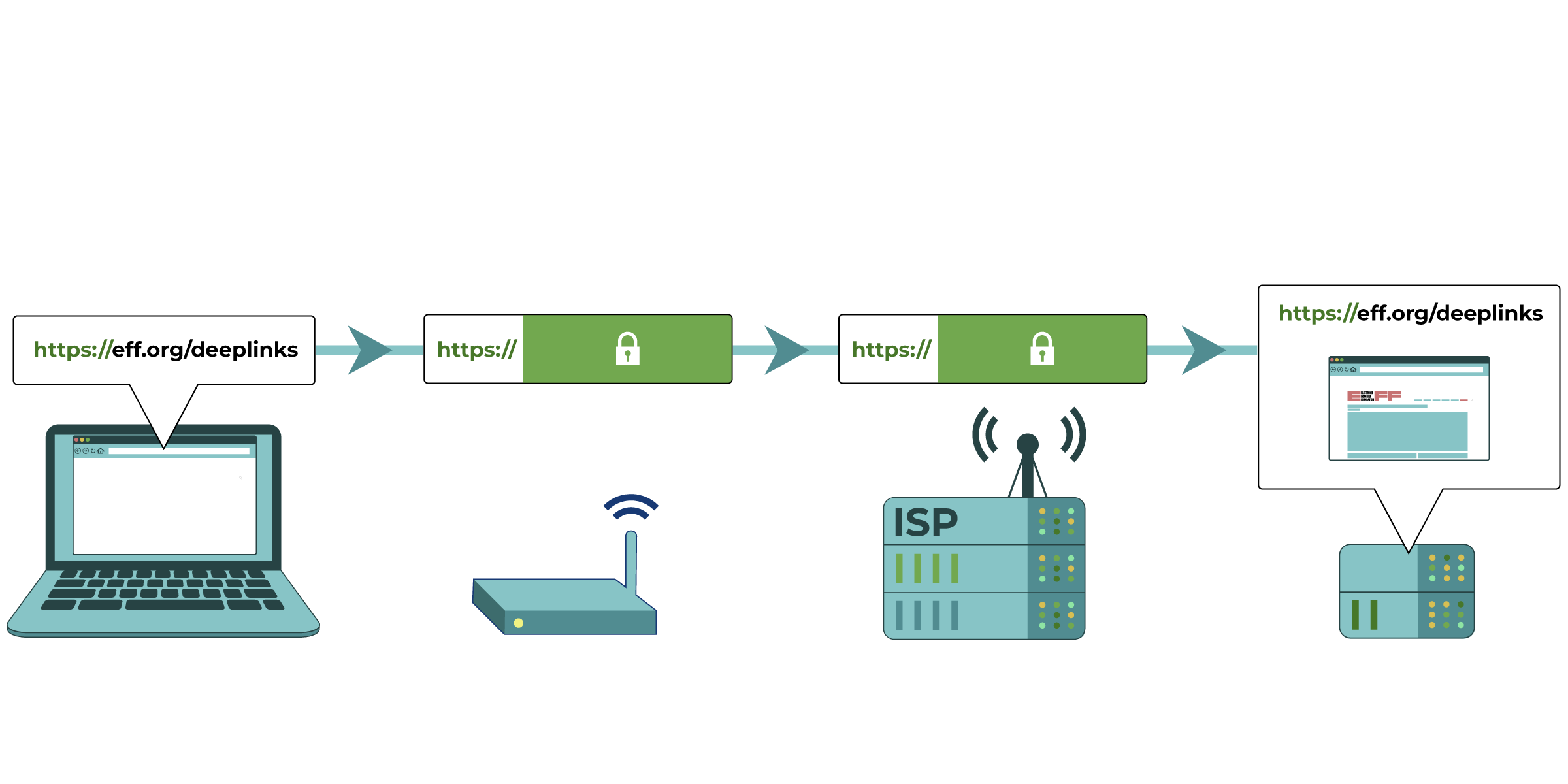
, and it is a form of censorship. Filtering comes in different forms. Even with encryption , censors can block entire websites, hosting providers, or internet technologies. Sometimes, content is blocked based on the keywords it contains. When sites aren’t encrypted, censors can also block individual web pages.
, censors can block entire websites, hosting providers, or internet technologies. Sometimes, content is blocked based on the keywords it contains. When sites aren’t encrypted, censors can also block individual web pages.There are different ways of beating internet censorship. Some protect you from surveillance, but many do not. When someone who controls your net connection filters or blocks a site, you can almost always use a circumvention tool to get to the information you need.
Note: circumvention tools that promise privacy or security are not always private or secure. And tools that use terms like “anonymizer” do not always keep your identity completely secret.
The circumvention tool that is best for you depends on your security plan. If you’re not sure how to create a security plan, start here. While creating a security plan, be aware that someone who controls your internet connection may notice that you are using a particular circumvention tool or technique, and take action against you or others.
In this guide, we’ll talk about understanding internet censorship, who can perform it, and how it happens, before moving onto what you can do to get around it.
- Understanding Internet Censorship and Surveillance
- Censorship and Surveillance: Two Sides of the Same Coin
- The Cost of Surveillance
- Where and How Network Censorship and Surveillance Happen
- Where Is the Blocking Happening?
- How Is it Happening?
- Circumvention Techniques
- Change your DNS Provider to Access Blocked Websites or Services
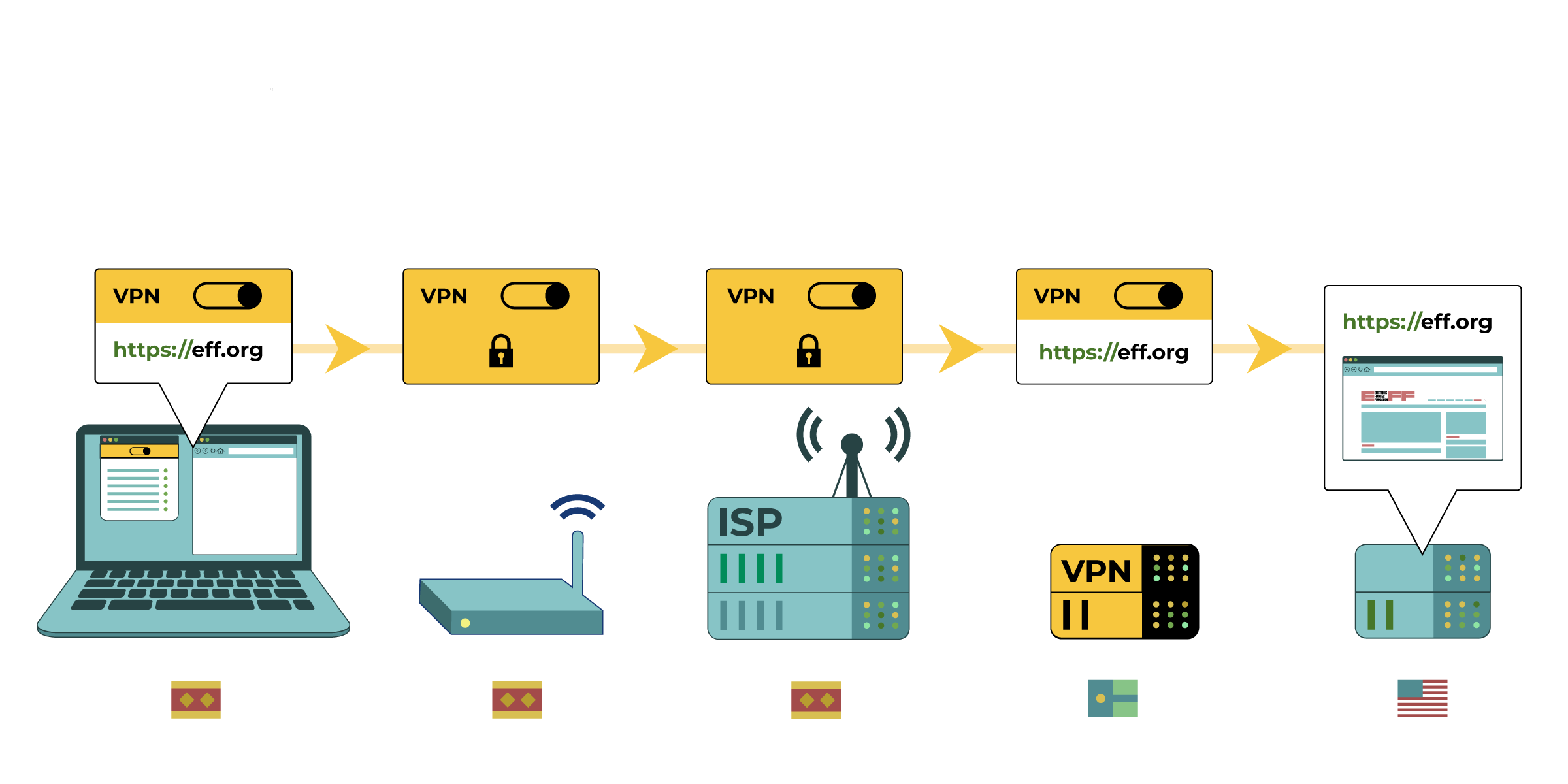
- Use a Virtual Private Network
 ( VPN
( VPN
 )
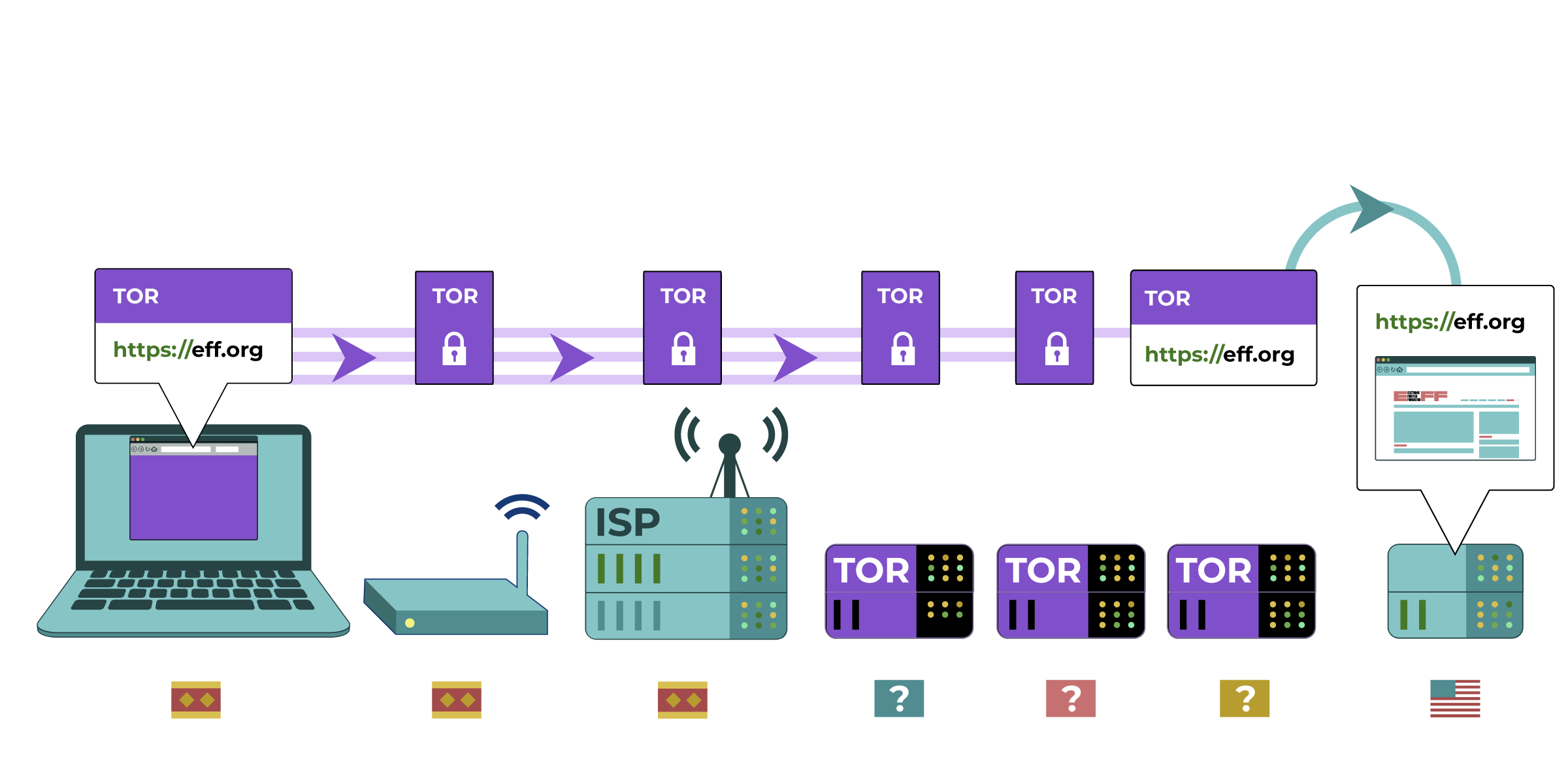
) - Use the Tor Browser to Access a Blocked Website or to Protect Your Identity.
- Use a Proxy Server for Messaging Apps
Understanding Internet Censorship and Surveillance anchor link
The internet has a lot of processes that all have to work together properly in order to get your communications from one place to another. If someone is trying to block parts of the internet, or particular activities, they may target many different parts of the system. The methods they use may depend on what technology and devices they have control over, their knowledge, their resources, and whether they are in a position of power to tell others what to do.Surveillance and Censorship: Two Sides of the Same Coin anchor link
Internet surveillance and censorship go hand-in-hand. Internet censorship is a two-step process:- Spot “unacceptable” activity
- Block “unacceptable” activity
Spotting “unacceptable” activity is the same as internet surveillance. If network administrators can see where you’re going on the internet, they can decide whether to block it. By advocating for internet and data
 privacy tools and technologies, we can also make internet filtering and blocking more difficult.
privacy tools and technologies, we can also make internet filtering and blocking more difficult.Many circumvention techniques have the additional benefit of protecting your information from network eavesdroppers when you go online.
The Cost of Surveillance anchor link
Blocking internet traffic comes at a cost, and over-blocking can come at an even greater cost. A popular example is that the Chinese government does not censor GitHub’s website, even though many anti-government newsletters are hosted on the website. Software developers need access to GitHub to perform work that is beneficial to the Chinese economy. Right now, these censors have decided that it will cost them more to block Github than they would gain by blocking it.Not all censors would make the same decision. For example, temporary internet blackouts are becoming increasingly common, even though these measures can seriously harm local economies.
Where and How Censorship and Surveillance Happen anchor link
Where Is the Blocking Happening? anchor link
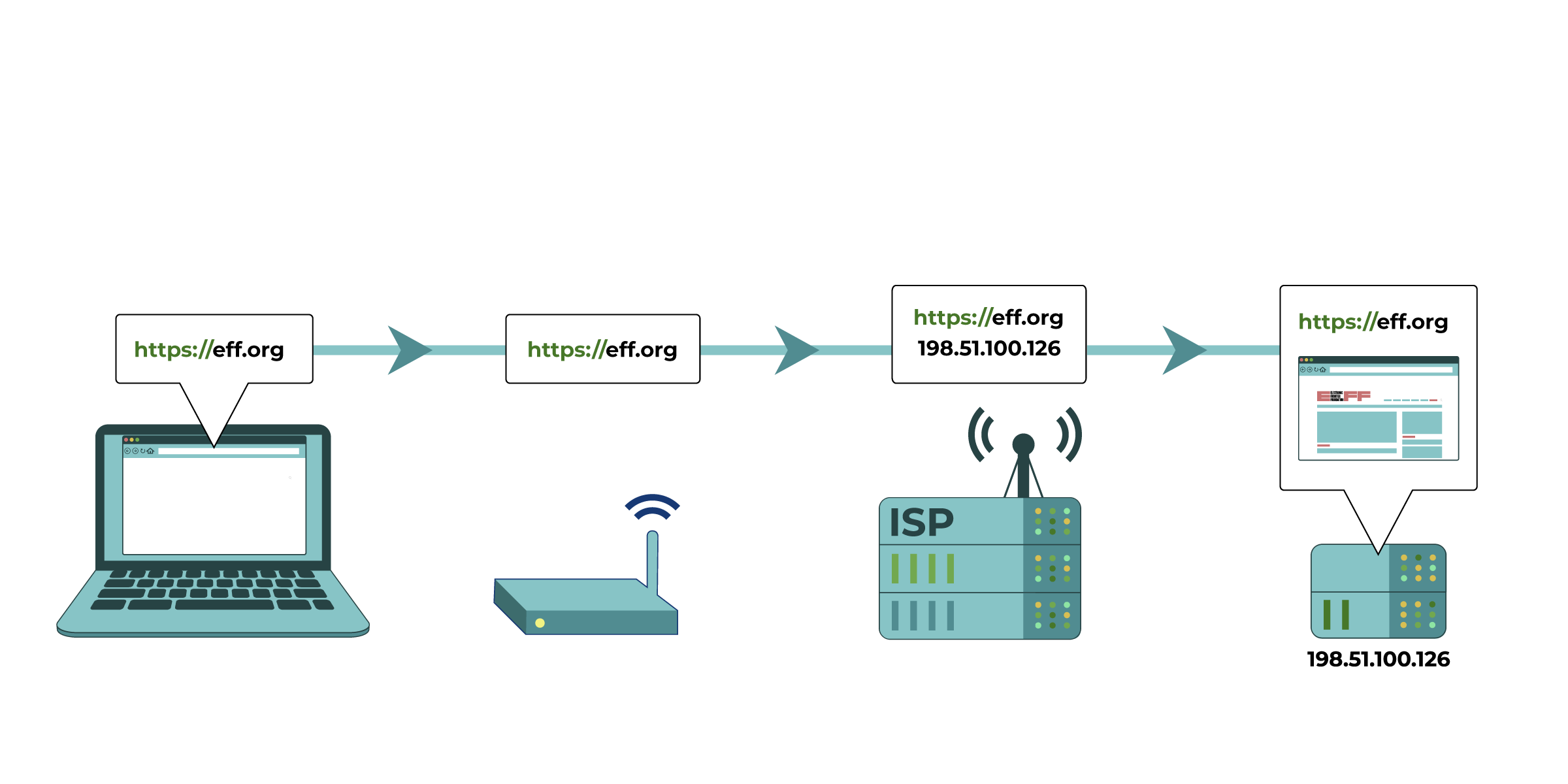
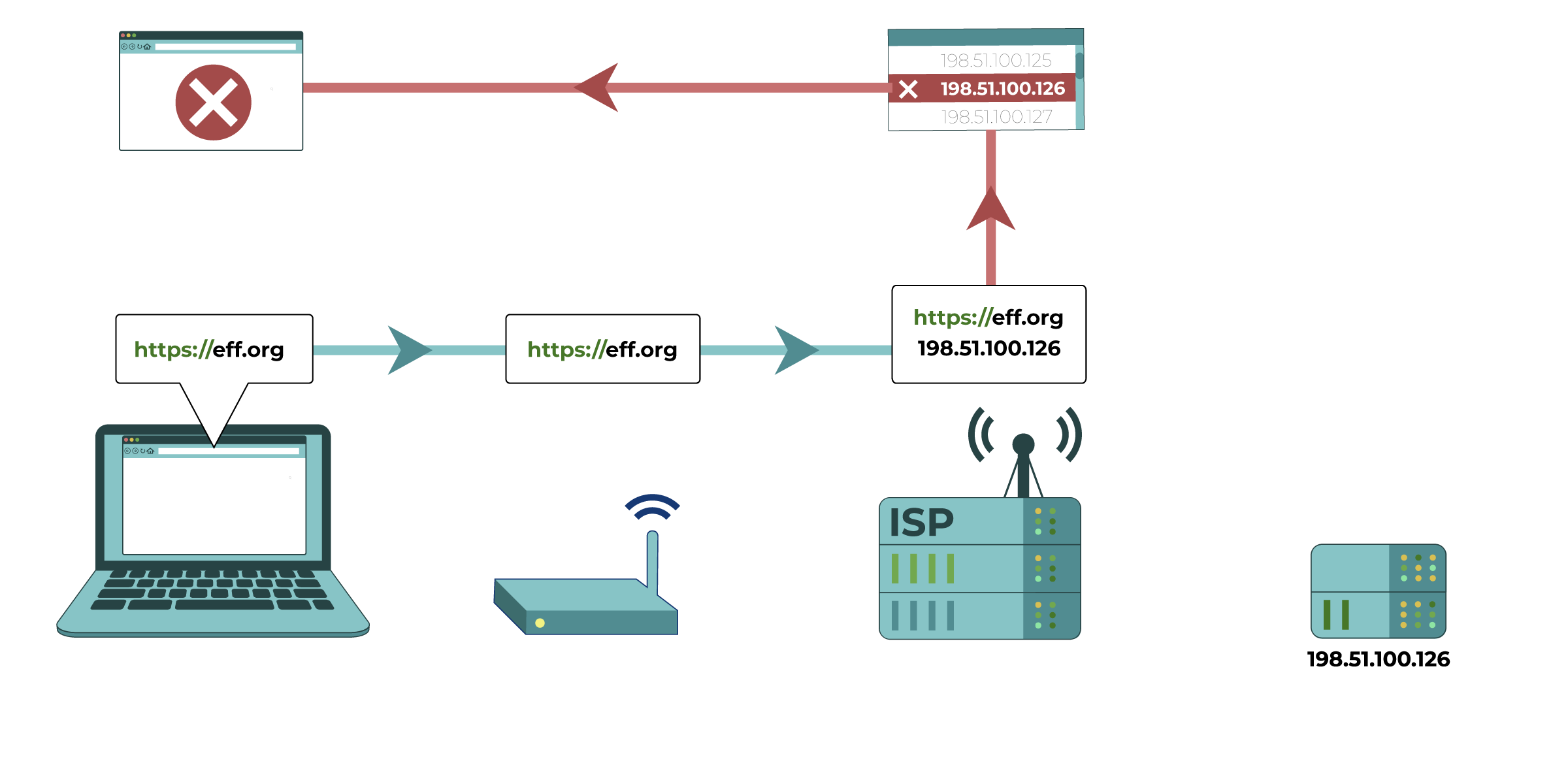
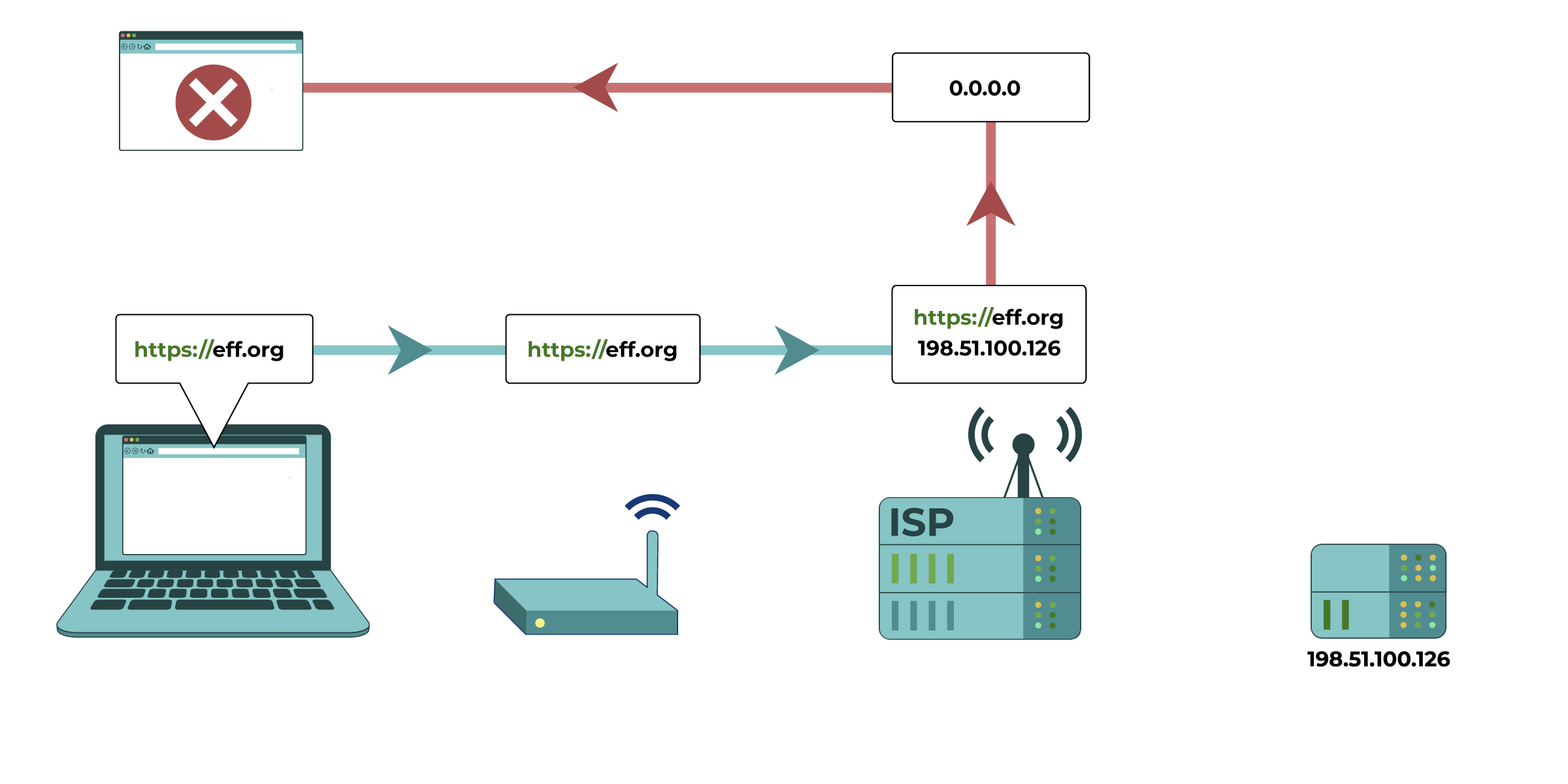
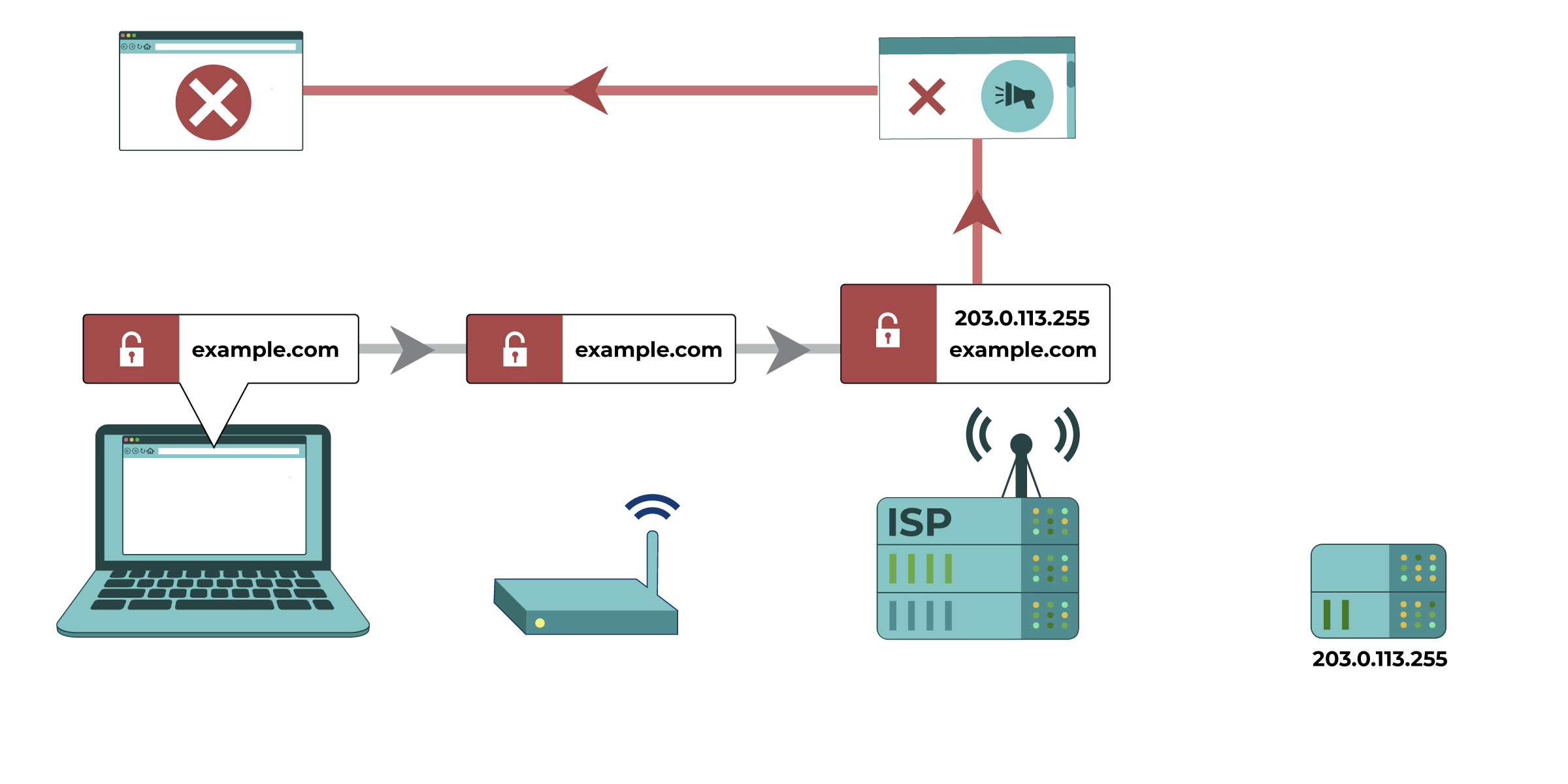
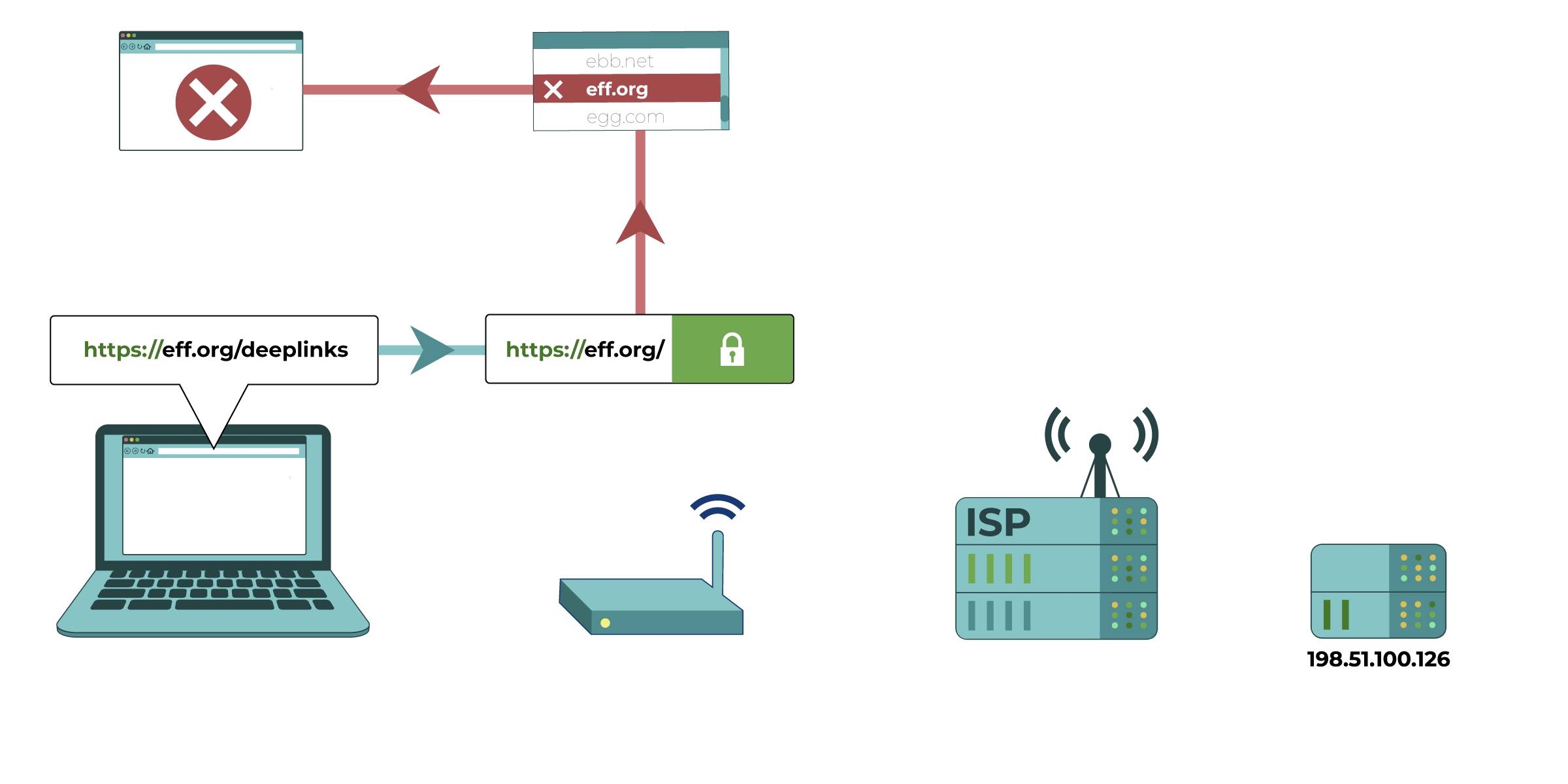
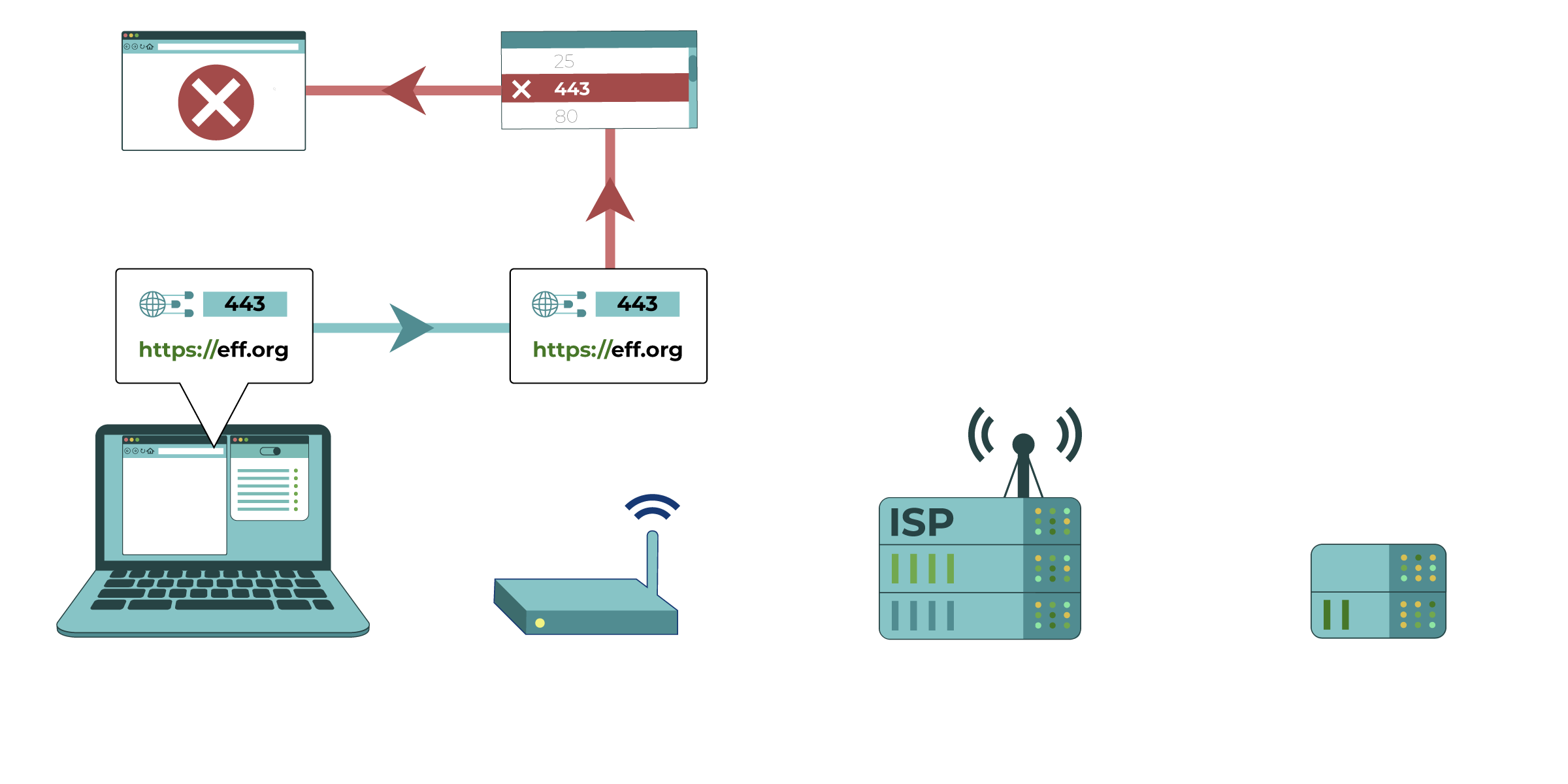
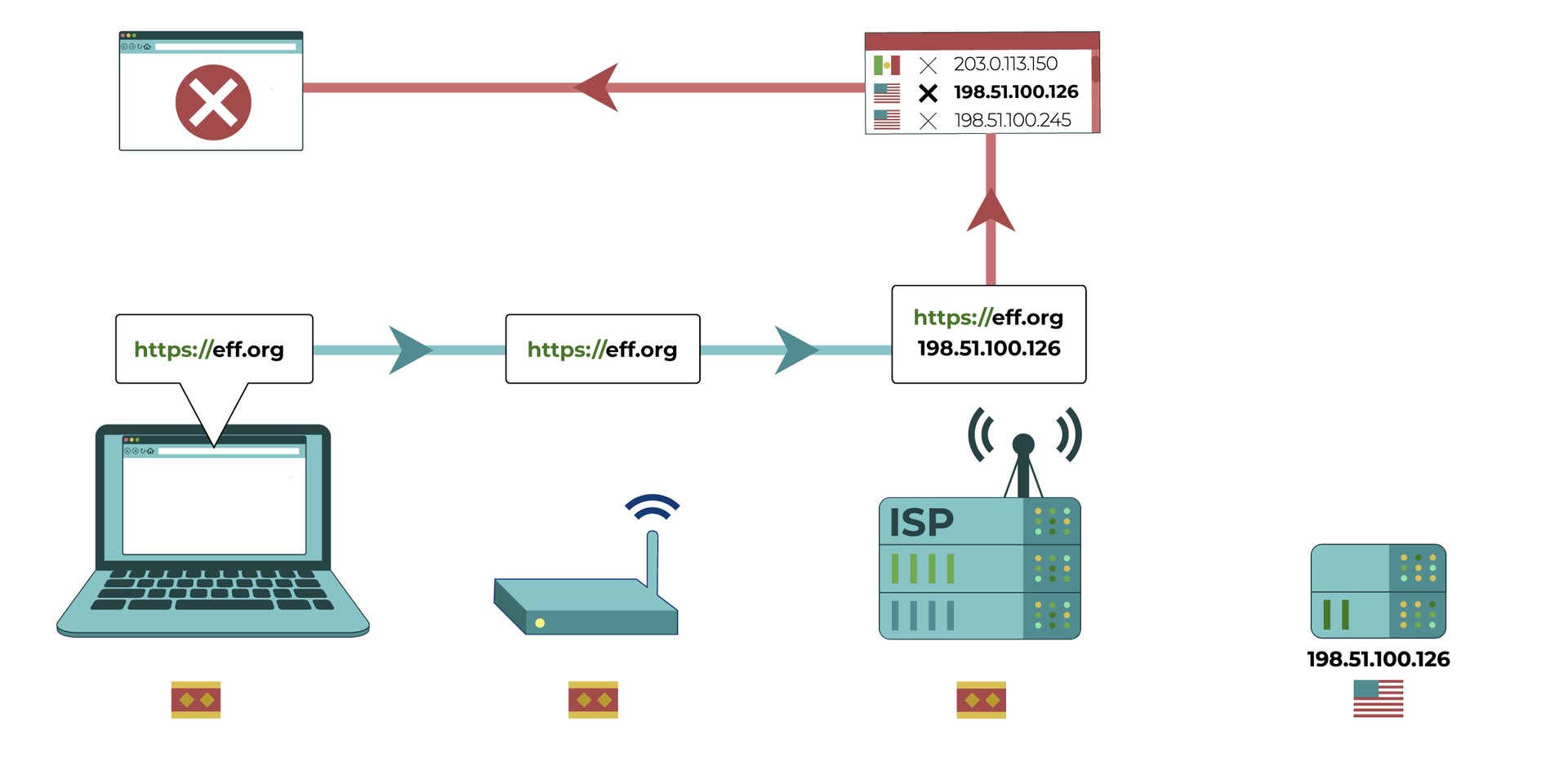
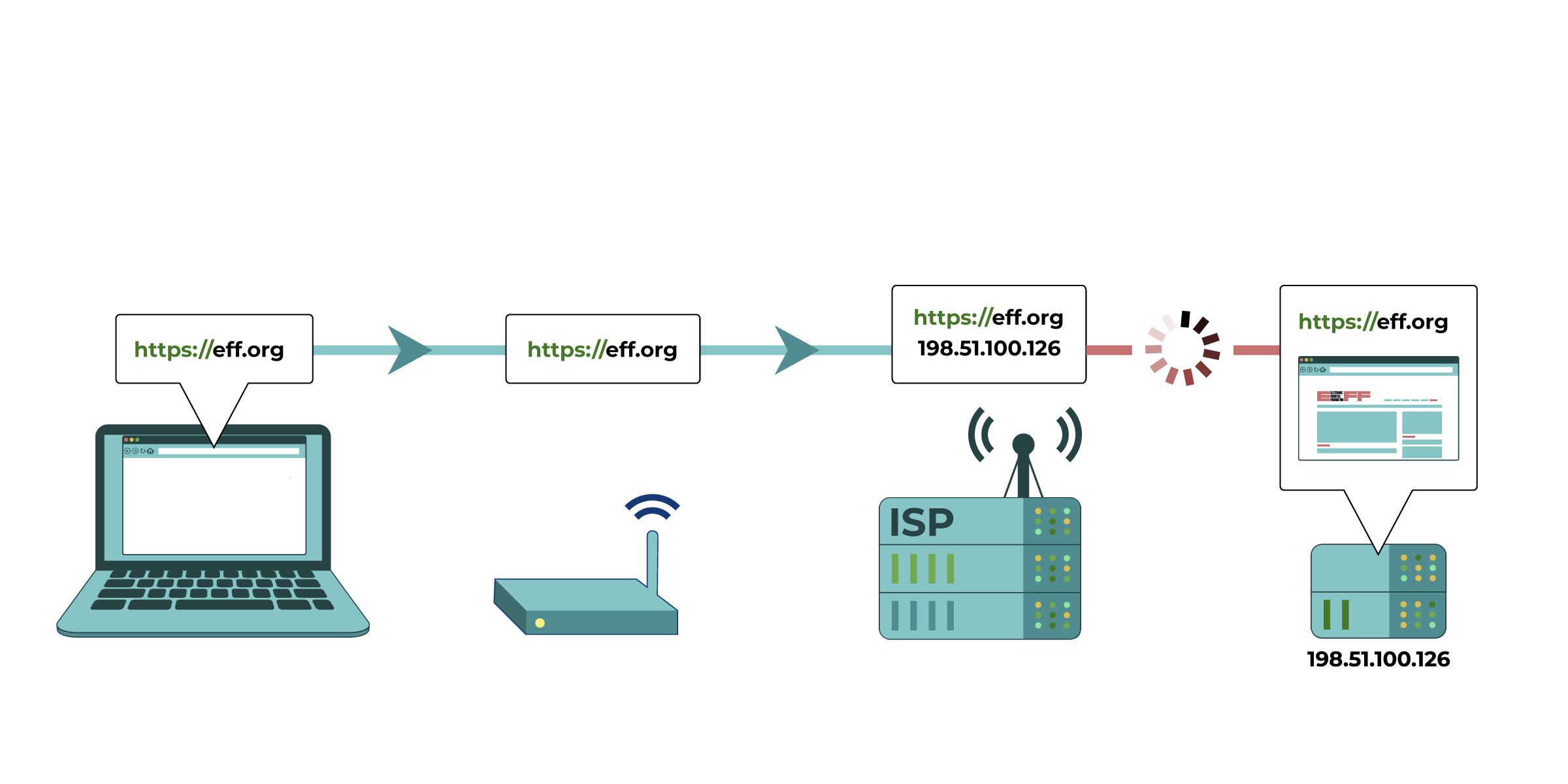
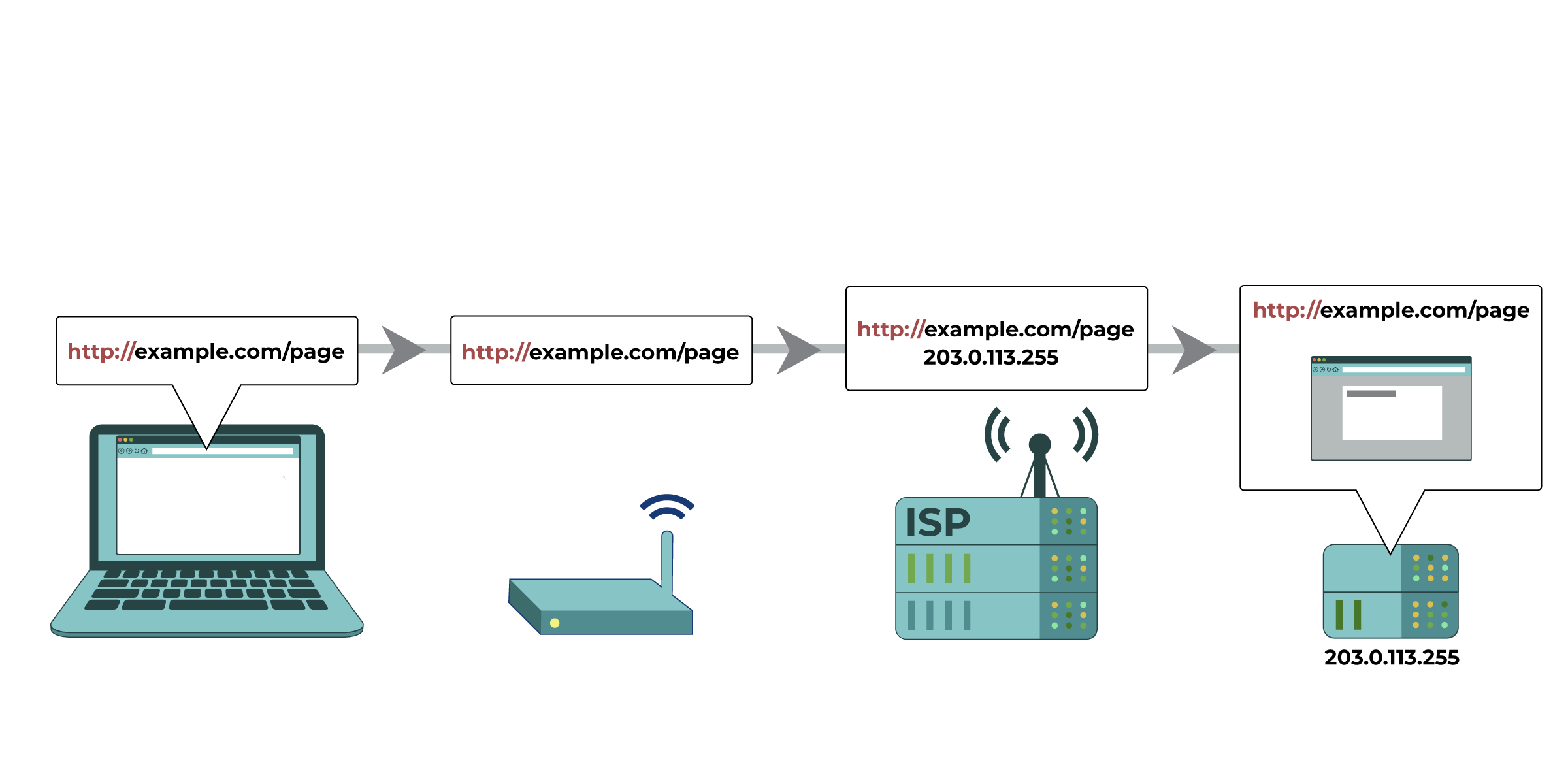
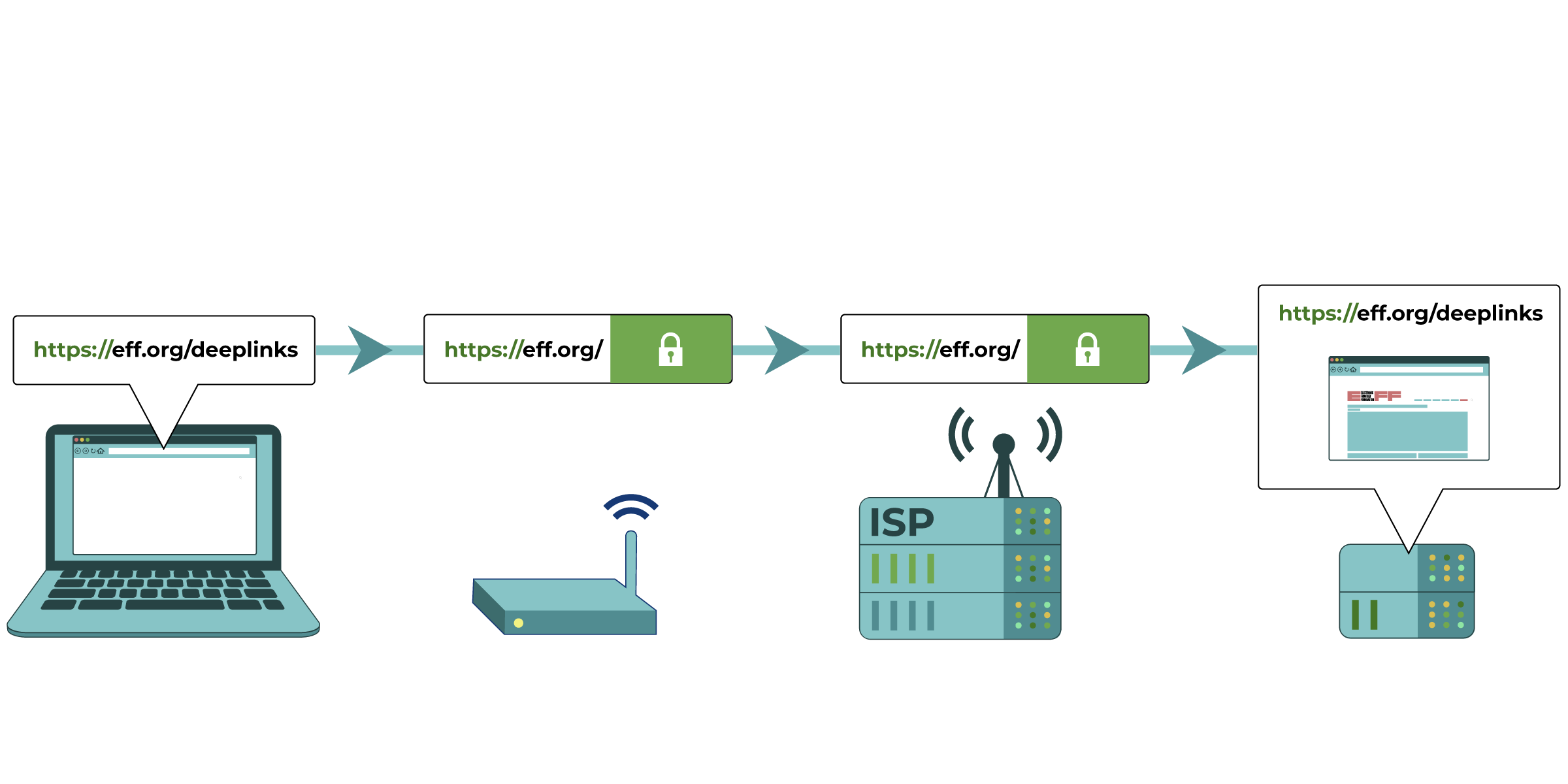
Your computer tries to connect to https://eff.org, which is at a listed IP address
 (the numbered sequence beside the server associated with EFF’s website). The request for that website is made and passed along to various devices, such as your home network router and your Internet Service Provider (ISP), before reaching the intended IP address of https://eff.org. The website successfully loads for your computer.
(the numbered sequence beside the server associated with EFF’s website). The request for that website is made and passed along to various devices, such as your home network router and your Internet Service Provider (ISP), before reaching the intended IP address of https://eff.org. The website successfully loads for your computer.
(1) Blocking or filtering on your devices. This is especially common in schools and workplaces. Someone who sets up or manages your computers and phones can put software on them that limits how they can be used. The software changes how the device works and can make it unable to access certain sites, or to communicate online in certain ways. Spyware can work in a very similar way.
(2) Local network filtering. This is also common in schools and workplaces. Someone who manages your local network (like a WiFi network) enforces some limits on your internet activity, like monitoring or controlling where you go online or when searching for certain keywords.
(3) Blocking or filtering by Internet Service Providers (ISPs). Your ISP can generally perform the same type of filtering as the administrator of your local network. ISPs in many countries are compelled by their government to perform regular internet filtering and censorship. Commercial ISPs can perform filtering as a service for households or employers. Particular residential internet service providers may market filtered connections directly to customers as an option, and automatically apply specific censorship methods (like those described below) to all connections on their ISPs. They may do this even if it isn’t required by a government, because some of their customers want it.