Data Patterns Suggest Trump Tower/Spectrum Health Ran a “Stealth Data Machine” With Russia
Data Patterns Suggest Trump Tower/Spectrum Health Ran a “Stealth Data Machine” With Russia
We pull back the curtain on Jared Kushner’s “Stealth Data Machine.”
Jared Kushner is currently taking a victory lap, crowin’ about his “Stealth Data Machine” that put Donald Trump over the top in the 2016 race. Let’s pry off the lid and peer into the inner-workings of this “Data Machine.”
The Signal in the Noise
Building on the work of
@LouiseMensch and data analysis by
@Conspirator0 on Twitter, Tea Pain has stumbled onto a possible “signal in the noise” that opens a window into the data-swappin’ shenanigans going on between Trump Tower, Spectrum Health and Russia’s Alfa Bank during the election.
Spectrum Health, owned by Michigan’s powerful Devos family, attempted to explain the IP activity as “Voice over IP traffic”, whereas Alfa Bank offered an even more exotic explanation that “hackers attempted to make it look like we contacted Trump Tower.”
The data traffic, when analyzed, tells a very different story, a story of automated, orchestrated data sharing among multiple sites for a strategic end.
Tea Pain originally dismissed this story as a possible red-herring. With the Russia craze at a fever pitch, this activity could be explained by what Tea’s daddy used to say, “When you got a new hammer, everything looks like a nail.” But when Tea Pain saw the data patterns analyzed by Conspiritor0, he knew he’d spotted something mighty familiar: Database Replication. Put a pin in that, more on that later.
At first, data analysts were puzzled by what appeared to be random activity with no apparent pattern. Perhaps it was email activity? Maybe money transfers? But there were literally thousands of these IP “pings.”
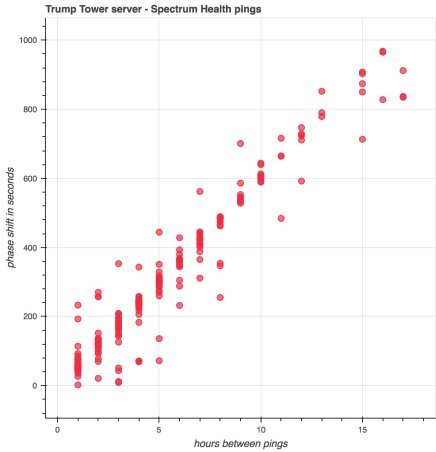
Once the activity was charted, a pattern emerged. For example, a connection is made from Alfa Bank to Trump Tower, which may last anywhere from 1 minute to 15 minutes or more, followed by a longer “sleep” period. When averaged over months, these events charted an average time between connections to be 3660 seconds, or 1 hour and 1 minute. Whatever was running, it would hook up, transfer data for a few minutes, then go to sleep for an hour.
This was the clue that led Tea Pain to formulate a much clearer working model to explain what we were all seeing: SQL Server Database Replication between multiple sites.
What Is Database Replication?
Database Replication is a rather simple concept. When you have a database with millions of records representing hundreds of gigabytes of data, and you would like to keep a copy of that database housed in 2 or more locations, it makes no sense to continually copy the entire database from point A to point B every time a change is made, so you “replicate” it.
This allows only the changes made to be sent from one database to another. This is accomplished by a process that runs on timely intervals, usually an hour, that wakes up and checks the changes made since the last hour and broadcasts those changes to the other database. The other database, in turn, check for its changes and broadcasts them in the other direction. Voila! Both database are identical!
So what does the data traffic patterns suggest? Check out the chart below. Behold, Kushner’s “Stealth Data Machine.”
The white box illustrates the scope of data we can now observe. The bulk of the replication took place between Trump Tower and Alfa Bank, while smaller amounts of data were transferred between Trump Tower and Spectrum Health. If, for example, Trump Tower talked to Alfa Bank for 10 minutes, the next Spectrum-Trump Tower connection might last only one minute, indicating data replicated from Trump Tower to the Devos health care empire was being filtered, perhaps by “WHERE StateCode=’MI'” for example. But when changes were made at Spectrum, things looked very different.
Conspiritor0 noted that when Spectrum connected to Trump Tower, Trump Tower’s next connect time was significantly longer, indicating Spectrum had modified a large chunk of records that had to be synced to Trump Tower, then pushed on to Alfa Bank. This detail was important in identifying that replication was in use. In this scenario, Trump Tower was functioning as a center-point, a data-distribution center if you will.
We don’t know what was in these data packets; that info is beyond our purview at this time, but ask yourself a simple question and you find your answer: “What does Trump Tower, the Devos Family and the Russians all have in common? A desire for Donald Trump to be President of the United States.
Tea Pain’s working theory is that Russia created a voter targeting database with information gleaned from hacked DNC data rolls and other data rolls “acquired” from other states to feed this growing contact database. That database originated at Russian Intelligence which was in turn replicated to Russia’s Alfa Bank. This is where the “data laundering” takes place, Alfa Bank is the pivot point where the FSB’s data fingerprints are wiped clean. Ironically Russia launders its data at the same place it launders its money.
In New York Trump Tower could merge data into this system using various legal sources as well. Spectrum Health could also add value to the data by matching names and addresses in their extensive healthcare databases to harvest email addresses and phone numbers to flesh out this list. All these changes would be promptly replicated back to Russia in a matter of hours.
Once back in the hands of Russian Intelligence, this massaged data could be programmatically matched up with social media handles to create a micro-targeted “hit list” for the thousand Russian trolls employed by Putin.
The Payoff
How is this a breakthrough? Now that we have identified the likely means of how this data was transferred, data analysts now have more precise points to search for to arrive at a complete reveal of the massive data collusion between Team Trump and America’s foremost adversary.
The “beauty” of this system is its simplicity. Here’s some bullet-points to sum up.
- No special software needed. SQL Server is used in most every major enterprise. Replication is a built-in tool. No mysterious hidden processes, viruses, malware, etc.
- Virtually undetectable. No one would blink an eye at data replication, a standard business practice.
- Could all be set up remotely with only VPN credentials and remote desktop access, information that is often shared via routine third-party data audits. No one inside Trump Tower or Spectrum’s IT department need be involved. One Russian Intelligence data operative could set this up in less than an hour at each location. No low-level “conspirators” needed.
- Value could be added to the data anywhere in the chain and it would promote back to Russian Intelligence within 2-3 hours.
- All data-transmission would be out in the open, mixed in with the daily flow of business.
- Even if found, the data would look benign, just names, addresses, phone numbers, email addresses, social media handles, etc. No financial information. It would look just like a contact lead database purchased from any data-mining merchant.
- Trump/Spectrum operatives and employees in the United States could interact with this list and have no clue the origins of the data were nefarious. This plain-sight approach was the key to its success.
@DonKnock @Hood Critic @LHilla @ReignAsKing @True Blue Moon @poRATCHETteacha @Sammy Steez @SJUGrad13 @88m3 @lotuseater80 @Cali_livin @Cobratron @Menelik II @RJY33 @greenygreen @jerniebert @Wepa Man @PlayerNinety_Nine @AZBeauty @Hogan in the Wolfpac @iceberg_is_on_fire @Airfeezy @wire28 @Atlrocafella @Ss4gogeta0 @smitty22 @Ms. Elaine @Reality @fact @Hood Critic @ExodusNirvana @re'up @Call Me James @Blessed Is the Man @BaggerofTea @GnauzBookOfRhymes @THE MACHINE @OneManGang

and yall believe it too